On April 21st AeroDefense kicked off a three part webinar series. The overall topic - Airspace Security Is A Process, Not a Technology. In a nutshell, in order to effectively combat drone threats you need more than just technology. Throughout the series we discussed the critical aspects of that "process.”
In our first session, Adam Schenkel with Deloitte’s US Drone Services practice covered drone threat risk management strategy, the regulatory environment surrounding drone detection and mitigation technology, and response planning best practices.
Here are some highlights from Adam's presentation.
Why risk management for drone threats is so important
Risk management can be defined as the process for identifying, planning, responding, and monitoring risks to an organization.
Risk management can help you answer the question – why do I need a drone detection or counter Uncrewed Aerial System (cUAS) system?
Understanding the reasoning behind a decision to acquire a capability to counter drone threats should be firmly based on the realistic risk posed to the organization by drones themselves.
Risk can take many forms, such as the threat of harm to people, disruption to economic activities such as at sports events or airports or the use of drones to conduct unwanted remote monitoring activity.
Lastly, pulling together an understanding of why a drone detection system is needed and correlating that understanding with a realistic understanding of drone threats will enable organizations to identify the right system to meet their risk profile and requirements. As an example, acquiring systems with capabilities which far exceed an organization's risk profile from drone threats may be an unnecessary expense.
A Risk Management Approach
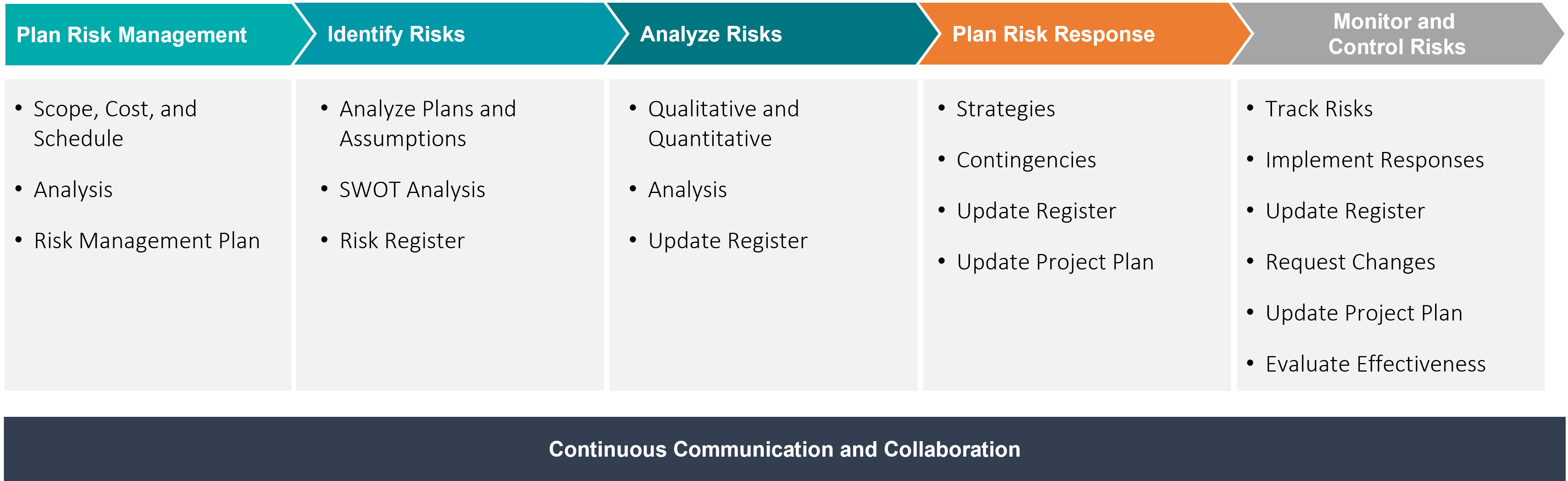 There is a five-step process to understand and assess risk and to also provide for the continuous monitoring and management of risk once identified.
There is a five-step process to understand and assess risk and to also provide for the continuous monitoring and management of risk once identified.
Step 1 As with many processes and frameworks, the first step should normally be planning and ensuring there is an understanding of the key components of the framework. One important item in the planning phase is identifying and defining the scope of the risk management identification process. When analyzing risk to an organization it can be easy to move outside the bounds of the initially identified scope, such as drone threats.
Step 2 The second step in the framework involves the identification of risk which can include different processes such as a SWOT analysis and should also be captured in a document such as a risk register.
Step 3 Once risks are identified it is time to analyze those risks through both a qualitative and quantitative lens. Risk analysis can include prioritization of the risks and weighting risk based on threat potential, likelihood of occurrence, or other defined metrics.
Step 4 Upon completion of the identification and analysis of drone threat risks, it is now time to plan an appropriate risk response which matches the organization's requirements. Risk response can take many forms, such as policy changes, the acquisition of new hardware capabilities, or physical changes to an organization's physical security posture.
Step 5 To close out this framework, it is also critical to routinely identify and analyze new risks to ensure an organization is current with its risk management posture. This is done through continuous monitoring and evaluation of drone related risk, on a routine basis which is appropriate for the organization's threat level.
Legal/Regulatory Environment
Drone detection and mitigation technologies are governed by U.S. federal law and informed by important policy considerations such as air safety, national security, and privacy.
Multiple US federal agencies jointly-published the Federal Advisory on the Application of Federal Laws to the Acquisition and Use of Technology to Detect and Mitigate Unmanned Aircraft Systems in August of 2020. The intent of the Advisory is to assist organizations as they navigate US law and regulations relevant to drone detection and cUAS systems.
The advisory addresses two categories of federal laws that apply to drone detection and mitigation:
-
-
- Provisions of the US criminal code enforced by Department of Justice (DOJ)
- Federal laws and regulations from Federal Aviation Administration (FAA), Department of Homeland Security (DHS), and Federal Communications Commission (FCC)
-
To assist the DOJ and DHS in combating drone threats, Congress passed the Preventing Emerging Threats Act of 2018 (codified at 6 U.S.C. § 124n) ("the Act"). The Act provides DOJ and DHS with a tailored grant of authority for authorized Department components to take certain counter-drone actions to mitigate credible drone threats to designated facilities and assets.
DOJ guidance clearly provides instructions for an authorized Department to operate protective measures without being prevented by provisions of law, namely 49 U.S.C. § 46502 (aircraft piracy), 18 U.S.C. § 32 (destruction of aircraft), 18 U.S.C. § 1030 (computer fraud), 18 U.S.C. § 1367 (interference with the operation of a satellite), and chapters 119 (interception of communications) and 206 (pen registers and trap and trace devices) of Title 18.
If an authorized Department component seeks to have a facility or asset designated as a covered facility or asset and deploy protective measures, the component head must submit a written request for approval to the Deputy Attorney General (the “Approving Official”).
If an authorized Department component wishes to make a significant change to a previously designated covered facility or asset or a previously authorized protective measure, it must submit a request to the Approving Official updating the information previously provided.
Changes to cUAS system settings must be coordinated in advance with the FAA and, when relevant, the National Telecommunications and Information Administration.
There is a significant level of effort required to deploy a mitigation and detection system at a covered facility, with minimal flexibility for system modifications. Organizations should consider if it may be more efficient to deploy RF-based drone detection systems not governed by 124n depending on the specific organizational security requirements and threat profile.
Response Planning
So how can an organization pull together a new drone detection or cUAS capability into their overall threat response planning framework?
We’ve just reviewed risk management and acquiring systems which fit into the legal and regulatory bounds of an organization. The logical next step is to integrate the new capability into an organization’s response planning, much in the same way as a fire evacuation or medical emergency plan are normal parts of prudent response planning.
The graphic below outlines an approach to a continuous capability development cycle which can be used when integrating drone detection or cUAS capabilities into an existing or newly developed response plan.
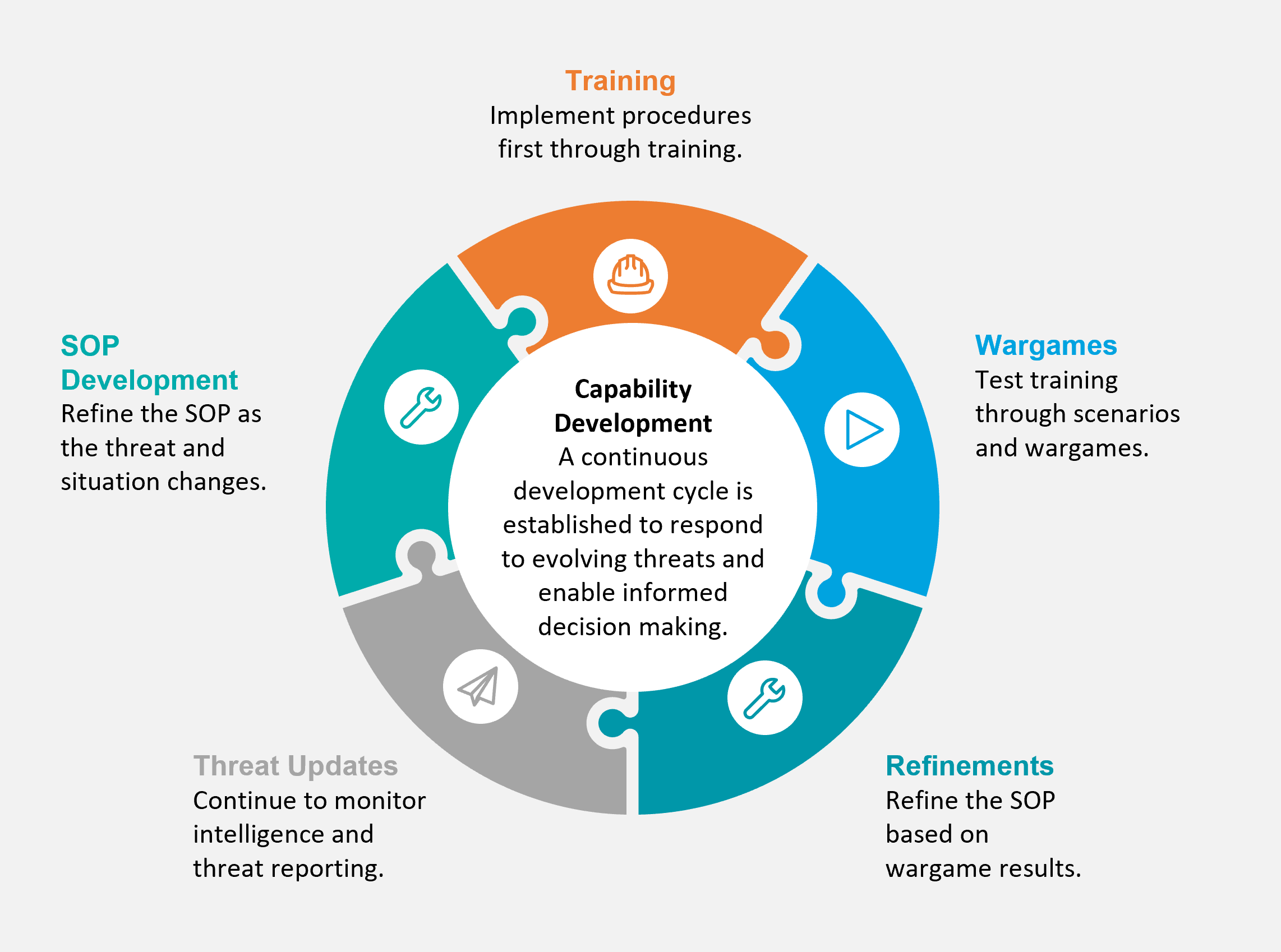 Developing a training program to ensure operators are familiar with a new system capability and the associated procedures for using a system is important to ensure the successful deployment of a new capability. Training also provides an opportunity to discuss capabilities and limitations of a new system and to help manage expectations about what a system can and can not do to a drone threat.
Developing a training program to ensure operators are familiar with a new system capability and the associated procedures for using a system is important to ensure the successful deployment of a new capability. Training also provides an opportunity to discuss capabilities and limitations of a new system and to help manage expectations about what a system can and can not do to a drone threat.
Looking at the right side of the graphic, a wargame event or tabletop exercise (TTX) can be designed to formalize and validate drone cUAS detection response procedures, coordination, and reporting through the use of realistic scenarios tailored to an organization's operating environment.
A war game and TTX methodology ensures optimal technology configuration and deployment to match an organization's drone threat response strategies and can also bring together stakeholders both internal and external to an organization which may be involved with a drone threat response.
As with a good risk management plan, response planning also requires continuous monitoring and refinement to ensure new threats are adequately accounted for with an organization's processes and procedures. These processes and procedures are normally codified in a Standard Operating Procedure (SOP) or other governing document to provide guidance on what to do in the event of a drone threat situation.
Response Planning Framework
The importance of having a framework can not be understated with Risk Management, and the same philosophy applies to building a drone detection response planning capability.
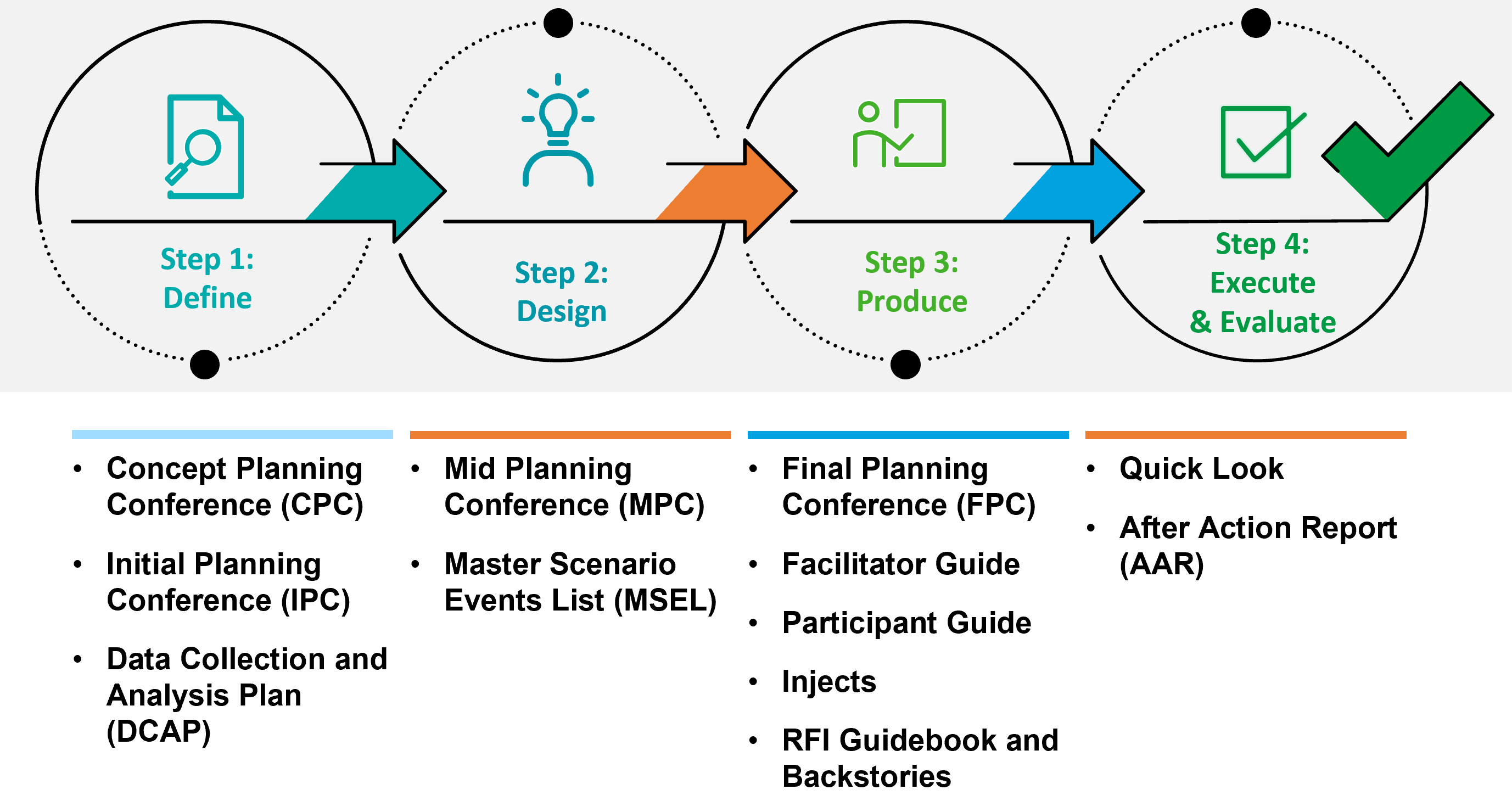
The four step response planning framework outlined above of Define, Design, Produce, and Execute & Evaluate is designed to encompass all steps necessary to adequately integrate a drone detection or counter-UAS capability at an organization.
These steps can be used in the development of wargame or TTX events, applied specifically to drone threats and the associated appropriate responses.
Integrating the response planning framework into wargame and TTX design will ensure a properly planned and executed event takes place and adequate value is achieved for all stakeholders who participate.
